
Call centers are still vital to the retail transaction process.
Solutions are out there, but for now it seems that fraud is rampant across this particular channel.
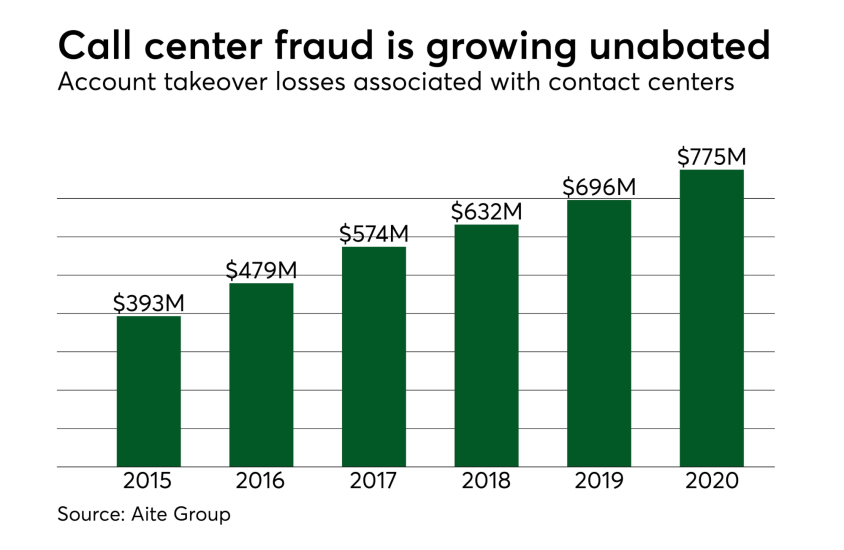
Is this rise attributable to a shift in fraudsters' modus operandi due to EMV’s role in mitigating card present fraud? As with online fraud, a straight cause and effect is too simple to imply — fraud is growing at a rate beyond what can be attributed to EMV.
“We believe the spike in fraud between 2015 to 2016 to partially be driven by EMV — and it’s not just coincidental, because we saw the exact same trend in the UK several years ago around the adoption of EMV cards in the UK,” says David Dewey, director of research at Pindrop.
However, others are less certain about causality.
“There was recognition in many financial institutions that contact centers were being attacked to enable cross-channel fraud well before EMV rollout,” says Shirley Inscoe, senior analyst at Aite Group. “Contact center fraud likely would have continued to flourish regardless of the EMV rollout, but due to it, fraudsters may be focusing on contact centers even more than they might have without the EMV impact.”
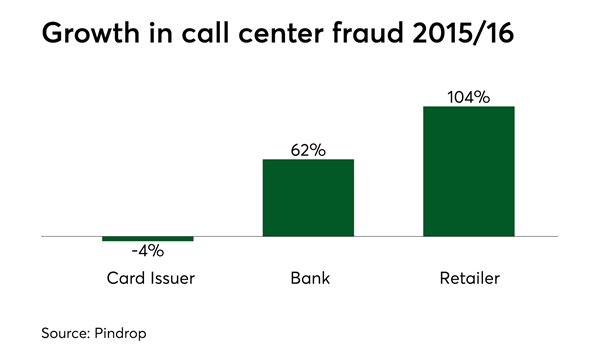
One would expect that a prime target for attacks would be card issuers' call centers, but according to Pindrop, these have actually experienced a 4% drop in fraud between 2015 and 2016. Others have been less fortunate — banks (in their non-card-issuing lines of business) have seen a 62% rise in call center fraud and retailers a staggering 104% increase in call center fraud between 2015 and 2016.
Fraud techniques are also shifting. According to Pindrop, in 2014, only 21% of fraud calls were made over mobile. Today, it’s 43%. This rise is likely due to the emergence of cheap “burner” phones, which many fraudsters assume to be untraceable. Additionally, spoofing can be done with much more ease. For example, fraudsters have the ability to spoof caller ID and use applications such as Skype or Google Voice to hide their identity and location.
“Hackers and fraudsters are becoming more devious, deceptive and simply smarter, manipulating call center agents and customer service representatives (CSRs) to steal and share customer payment card data and other sensitive information," says Tim Critchley, Semafone's CEO. “This could involve bribery, coercion, a fraudulent phone call or even a phishing email containing malware that an agent opens, thinking it’s a note from a customer or manager.”

According to an Aite Group survey of 25 executives at 18 of the 40 largest FIs in the U.S., various types of fraud were seen as major or critical issues. Nearly three quarters of respondents stated that access devices, social engineering and account takeover were major or critical issues for call centers, and over half cited transaction fraud as a major or critical issue.
While there are solutions to these types of attack, there appears to be some fundamental work to be done in training staff to treat card data and other forms of personally identifiable information (PII) with greater sensitivity.
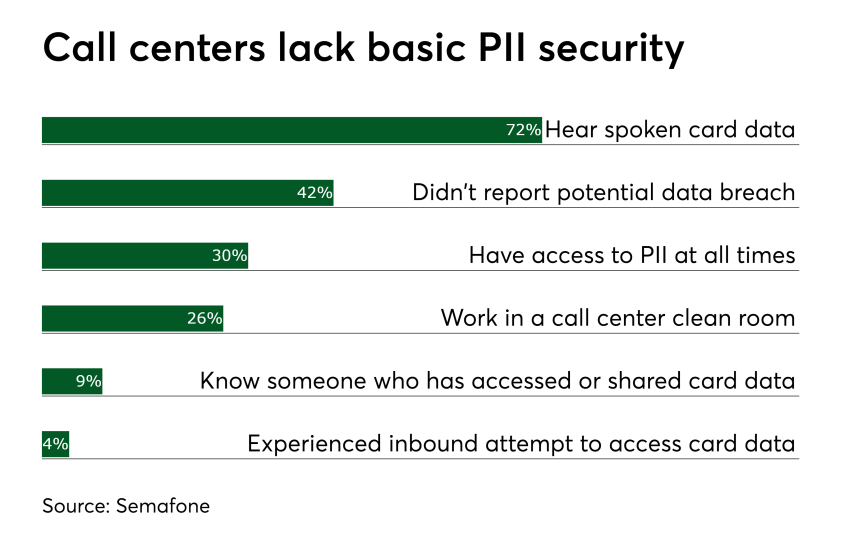
Equally alarming was that 42% of call center employees didn’t report a potential data breach internally, 9% know someone internally who accessed or shared card data without permission and a further 4% have experienced an inbound attempt to fraudulently access card data.
Some simple safeguards are also lacking. Thirty percent of call center employees stated that they have access to card data and other forms of customer PII at all times and only 26% of agents said they work in a contact center “clean room,” which prohibits personal items (cell phones, bags, pens and paper, etc.) and recording devices.
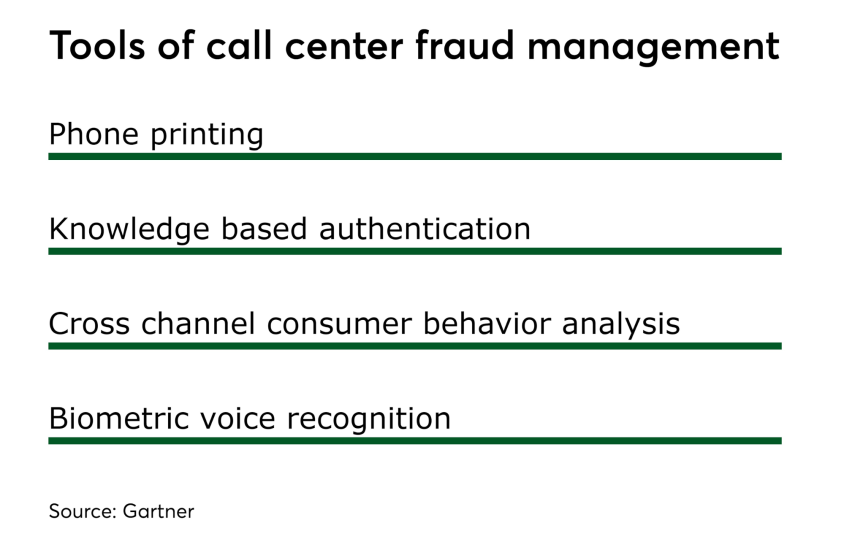
According to Gartner, advanced fraud attacks are multifaceted in their attack methods. This type of attack requires a layered and coordinated response with tools specific to the call center, as well as integrations with cross-channel consumer behavior analytics. Gartner outlines an infrastructure that includes phone printing, knowledge-based authentication of the caller, cross channel behavior analysis and biometric voice recognition.
However, there is no silver bullet and fraudsters are evolving their tactics to target high net worth customers and playing the long game, in much the same way as spear phishing evolved from phishing.
“We’ve found fraudsters are able to still penetrate these barriers — they will compile a dossier on a specific victim comprising high-quality data from many sources and then use that information in multiple interactions with a call center in an account takeover operation,” says David Dewey, director of research at Pindrop. “Additionally, the huge volume of stolen information available from data breaches means they have access to more accurate data about potential victims.”
The most secure way of protecting card data in call centers is by not handling or recording such data exposed in the first place. “They can’t hack the data you don’t hold,” says Tim Critchley, Semafone's CEO.





