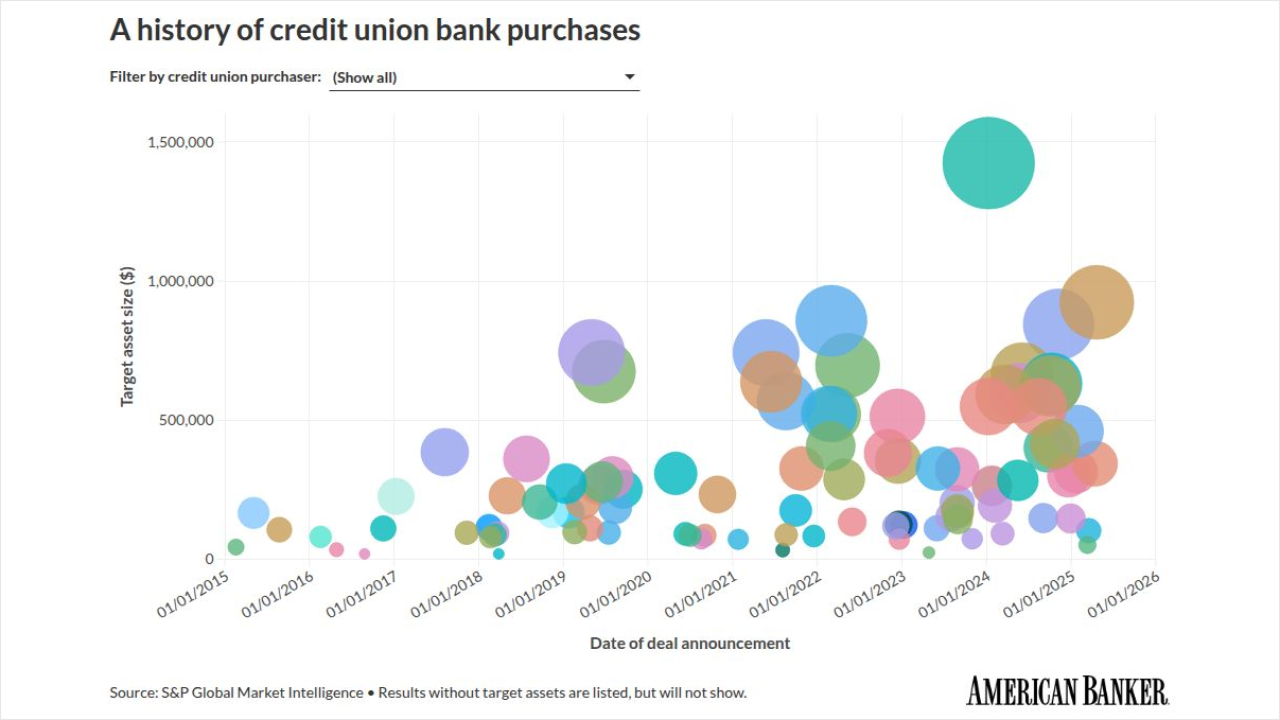
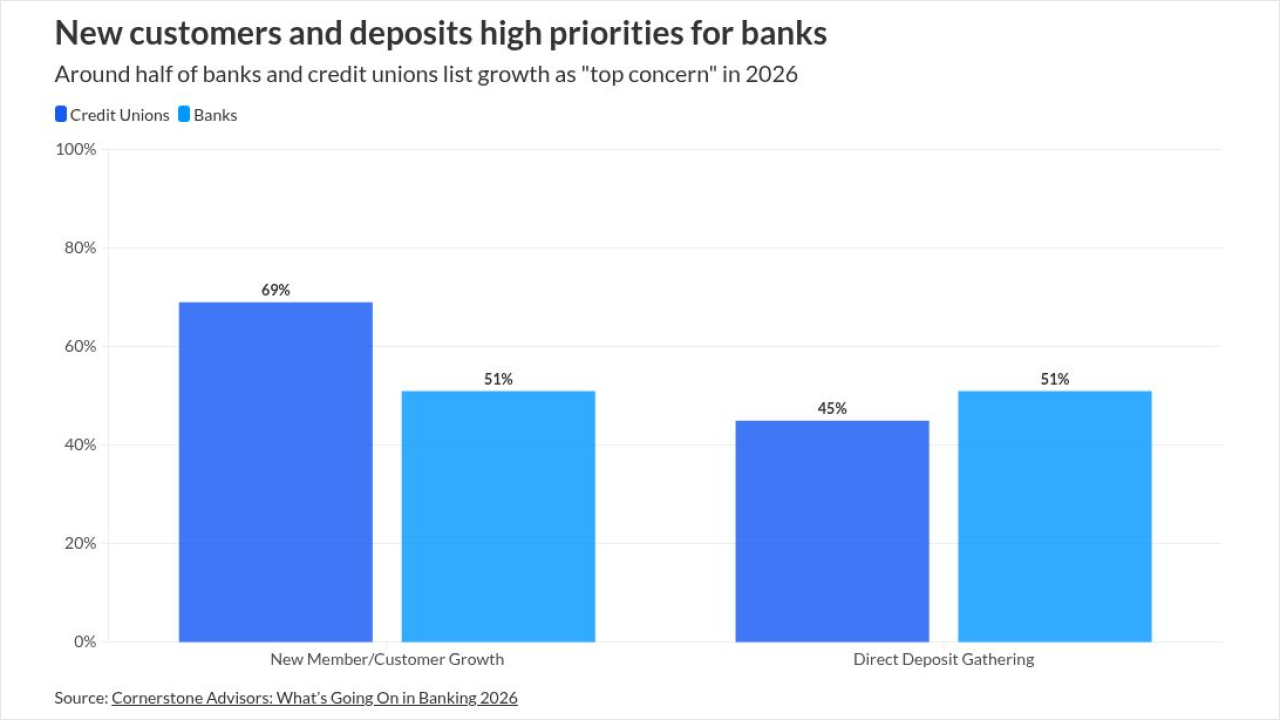
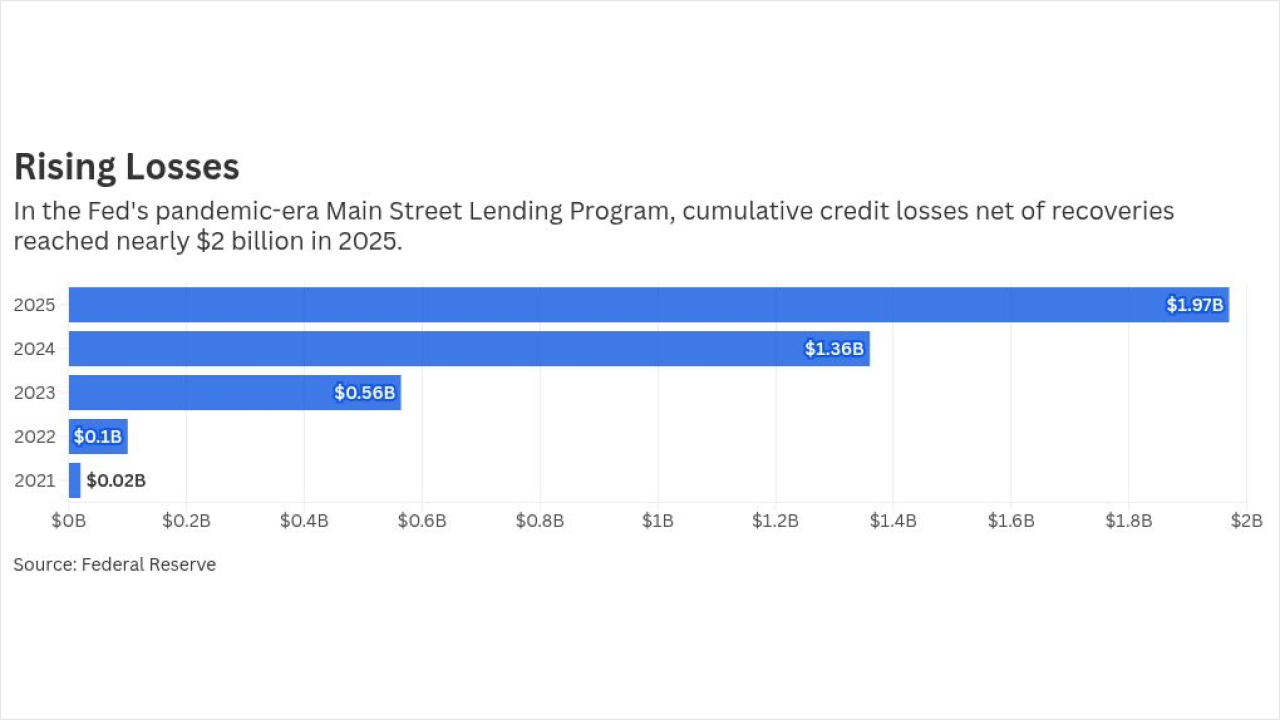
Ready or not, the frenzy of Black Friday, Cyber Monday and the overall holiday shopping season is upon us.
For retailers who can often earn up to 30% of their annual revenue in just the last two months of the year, the holiday shopping season can make or break annual projections. The National Retail Federation predicts that retail sales this November and December—excluding automobiles, gasoline and restaurants—will increase as much as 4%, reaching upward of $682 billion.
Unfortunately, this could be good news for fraudsters—if retailers don’t have the proper security and protocols in place to make sure nefarious players get a lump of coal instead of your organization’s data and holiday profits. Last year,
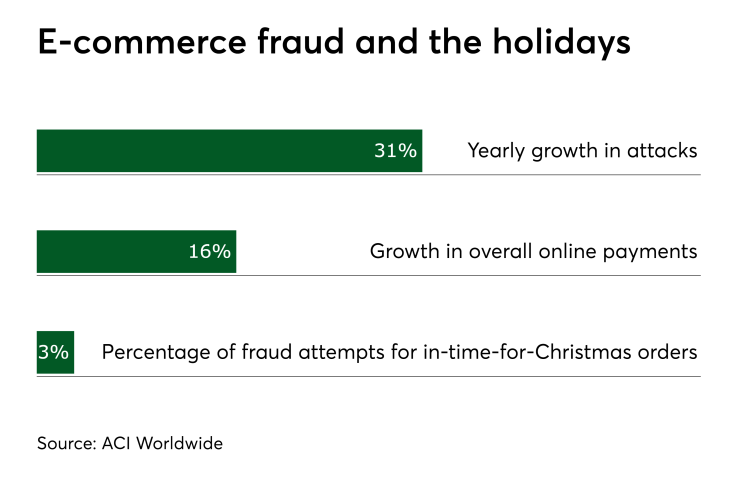
Combine those statistics with the increase in consumers using their mobile devices to conduct more transactions and it means retailers must step up their game and put security measures in place to diligently protect their profits, their reputations and their customers.
According to
Fortunately, retailers have an array of solutions available to combat increasing mobile fraud this holiday shopping season and beyond. By employing a multilayered approach to mobile security that combines device authentication with the latest user identification measures, retailers can establish maximum trust not only with their users, but also in the device being used to transact with them.
Here are some of the latest measures retailers can employ to mitigate the financial and reputational risks associated with mobile fraud:
User identification/biometrics. Passwords have been considered problematic within the information security community for a decade. The latest user identification best practices involve the use of biometrics to positively identify that users are who they say they are.
In recent years, the proliferation of fingerprint-enabled mobile devices in the market has provided new opportunities for mobile-enabled organizations of all types to leverage fingerprint biometrics as a more secure means of identifying good users. And the latest research shows that consumers are embracing the new technology.
Authentication by fingerprint solves customer frustration with passwords and strengthens security simultaneously, but fingerprint authentication is not truly secure if the device on which it operates can be easily compromised.
Device authentication. When the device itself is authenticated, the environment surrounding the transaction is secured. It is only when one trust the device and confirm the user’s identity that the—a trusted security token—can be created.
Device authentication involves many elements, including the creation of a permanent device ID, device integrity screening, secure storage and communications, device reputation analysis and more.
A permanent device ID is a way to identify a device and its riskiness. A mobile phone, for example, has thousands of unique identifying attributes that are part of the device itself and can be used to uncover and analyze risk factors that could lead to potentially fraudulent activities. A permanent device ID can survive an app uninstall/reinstall, as well as operating system upgrades. It also mitigates spoofing attempts. This makes a smartphone device itself a trusted second factor (something you have) of MFA. With a permanent ID, you can authenticate your trustworthy customers in a few invisible steps and risky devices can be challenged or stopped and blacklisted if they are associated with negative activity or fraud.
Device integrity screening attempts to analyze the health and integrity of a device—in other words, device risk. It can be one of the most accurate indicators of whether you can trust that this is the authorized user and approve, deny, or ask for additional authentication. In attempting to bypass common security techniques or compromise information, fraudsters leave indicators of their activity at the device layer. The best practice here is to deploy fraud detection capabilities that identify evidence of malware and other fraud tools used by criminals to defraud customers and hijack their account.
To prevent mobile communications from being intercepted, there must be a completely secure path to transport sensitive information that is encrypted end-to-end, digitally signed, cannot be read by any other device and is protected against replay attacks (secure communications). Sensitive communications must only be delivered to the intended device associated to a permanently-identified device. With the right encryption system, you can replace SMS and other non-secure communication by sending data via this encrypted path.
Device reputation analysis involves attempting to match attributes between mobile devices accessing your systems and known users. In situations where device reputation is completely unknown, such as during card provisioning, insight about the positive or negative history of the device transacting with your company becomes critical. If you can match that device with your own customer base, using a permanent identifier, then you have some insight into the correlation to the customer or the good or bad history.
Of course, behavioral analysis is always at the core of any fraud prevention approach. Behavioral analysis, for example, ensures the device is one typically associated with the customer, ensures the transaction activity is typical for this customer, and assumes an increased level of risk if this is a new account.
There are several important best practices here. Utilize advanced analytics, machine learning or fraud modeling to analyze your entire population of data to identify accounts with similar behaviors, past known fraud patterns, or customer identity and behavior patterns. For example, does the pattern of spending match typical spending patterns of the population, such as "is this customer purchasing many high value items quickly and is this typical for your consumers?"
With the right security solutions and best practices in place, your organization will be able to protect the key exposure points of traditional mobile payment offerings, enhance the success of credit card loads into any app, mobile wallet, cashless program or loyalty program, and deliver a frictionless experience for your holiday shoppers that will forge an atmosphere of trust, and repeat business, that will make 2017 a year for the record books.