Data security is a sensitive topic. Everyone wants to know the best way to stay secure…but no one wants to acknowledge that they may have a security issue.
When breaches happen, we tend to act as though it’s the product of deliberate negligence on the part of the brand involved. Of course, that’s rarely the case; most businesses and financial institutions that are hit by data breaches are doing everything they know to combat risk.
We need to work to both expand education on the topic of data breaches, and to destigmatize security concerns. Staying on top of new threat sources isn’t easy, but things will keep getting worse if we can’t openly discuss the matter.
At this point, awareness of widespread security vulnerability online is quite common. Even those who are not particularly tech-savvy have heard about high-profile data breaches involving names like Target, Equifax, Yahoo and many others.
But despite the extensive new coverage and an emphasis on security among consumers, these breaches continue to be a bigger problem than ever.
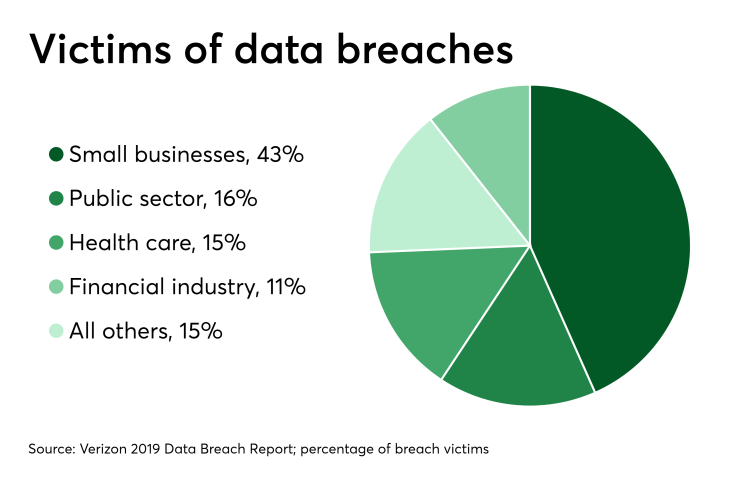
The recently-published
It’s not just that we’re seeing more attacks; we’re seeing individual breaches become bigger incidents. Of the 3,800 breaches reported in the first half of 2019, just eight incidents accounted for 80% of all compromised records. All totaled, though, we saw 3.2 billion individual records exposed in the first six months of the year.
What’s going on? Why are we seeing so many more hacking incidents, and what can we do to turn the tide against fraud?
A major part of the problem is simply the abundance of data floating. The problem is especially pronounced in the age of cloud computing.
Although security is a top priority, a breach can still happen. It’s just like identifying targets in a battle; storing any data offsite means you’re increasing your attack surface area, or your exposure to data breach, as there are more avenues through which you can be attacked.
Another common problem is security vulnerabilities that go undetected. For instance, old bugs or other issues that never get patched could be used against you by bad actors who exploit them.
It’s also worth noting that, despite consumers’ anxieties about fraud, they’re not very good at keeping their own data secure. Hackers know that the average consumer doesn’t really understand digital security. They know individuals often leave themselves open to attack by failing to adhere to security best practices. This creates a climate of paranoia among consumers, but it does little to improve actual conditions.
Is there anything we can do to address the issue? Fortunately, yes; as a matter of fact, there are several practices I recommend every business adopt to help mitigate the risk of data breaches, including:
Train employees on data security best practices. Keeping up to date with security shouldn’t be limited just to your security or IT departments. Everyone in your organization should receive regular training on data security best practices. This includes how to store and dispose of data securely, the importance of secure login credentials, and how to identify potential threats and vulnerabilities.
Encrypt All Data. You should develop a strong data encryption policy and enforce those standards on all devices connected to your network. No data, regardless of how insignificant it seems, should be stored or transferred in an unencrypted format.
Use Technologies Designed to Identify Intruders. Any systems that could be accessible via the internet should be protected by intrusion detection software. This includes all your internal servers, as well as any other systems that connect to them. Ideally you should have more than one detection tool in play; redundancy makes it possible to detect any threats faster.
Keep Up with Security Patching. Even if we know the importance of comprehensive security patching, we still often let our systems go without the most up-to-date patches. It’s not enough to enable automatic updates. You should keep tabs on your systems and download the new patch as soon as you learn about an update.
Monitor Insider Behavior. While many threats are external in nature, you can’t overlook the prospect that someone within your organization could be a bad actor. That’s why you must carefully monitor employees’ activities and watch for any suspicious behavior. Otherwise, you may not even realize that you’ve invited fraudsters into your home until it’s too late.





