Even before the COVID-19 pandemic forced retailers and consumers alike to consider the benefits of shopping via a mobile app, providers of shopping and loyalty apps were
But with the pandemic creating the need for a quick shift to digital commerce, not enough retailers are making security the top priority on their mobile apps. It's an oversight that could lead to financial burdens and consumer distrust, according to Grant Goodes, chief security scientist at Guardsquare, a mobile application security firm with offices in Leuven, Belgium and Boston.
"A mobile retail app is very similar to a financial, banking or payment app to attackers because credit cards are involved," Goodes said. "There is a giant target on these types of apps because you can get those credit card details if you are able to exploit the app."
The majority of retail apps lack basic security protections, according to Guardsquare research that assessed 51 of the top Android retail apps. The study focused on apps of which the majority were built for U.S. audiences, though some global in nature were included if they ranked highly in the Android marketplace.
Those targeting the apps are generally malicious actors collecting personal or financial data from the apps to use or sell, but Guardsquare also noted competitors seeking to gather intel or steal customer data from a retailer also pose a danger.
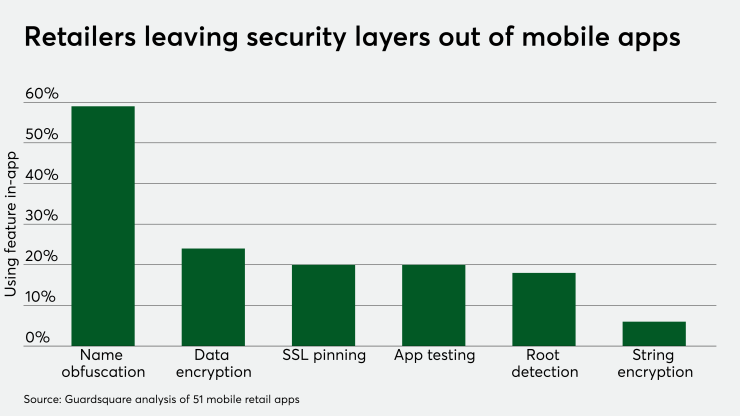
For the app analysis, Guardsquare established seven key protection areas retailers should have in place for their mobile apps.
Name obfuscation — or avoiding human-readable identifiers in the application's code — is a key factor, as too many apps had names like "for card processing" written into them. String encryption for sensitive text in the app is also important, especially for URLs, APIs or cryptographic keys.
It's also advisable to remove any visible APIs from the retail apps, as those may allow a competitor to discover a database for hotel guests or lists of a company's prices for various services or products.
Root detection thwarts an attacker from trying to bypass the application to give it commands from another computer or even a virtual device. In addition, all data at rest should be encrypted.
Finally, Secure Socket Layer pinning prevents man-in-the-middle attacks by validating server certificates, and app attestation helps assure both a device and an application that is running are genuine and that servers are not interacting with compromised endpoints.
The research revealed that 63% of the apps had just one or two of those seven key security features, while 23% of the apps had none of those protections. None had five or more.
"With the rush and speed to market for mobile apps because of COVID-19, it has caused security to become a secondary concern for some of these people, and that's reflected in the numbers in our report," Goodes said. "I would even say it is a little bit shocking as to how many apps have no security and how few have just good security."
The lack of security "really is quite striking," Goodes noted, considering the
The research found that of the 51 mobile apps assessed, seven were from companies already in bankruptcy protection and three of those apps had no security protections in place, Goodes added. "They were already in a situation of distress and they are putting out an app that could be hacked," he said.
In addition to payment and personal credentials, attackers eye rewards points, sometimes even on separate loyalty apps, because they can benefit by stealing them to spend or eventually sell, Goodes noted.
The lure of rewards, even more so than convenience and speed, has been the key factor for many consumers to turn to a mobile app. For several years now, the vast majority of consumers who have
Many companies have experimented with loyalty apps, feeling that maybe security wasn't as vital because they only store rewards points and the technology to cash them, not contact credit card information, Goodes said. "Much to their chagrin, they found out that these are also exploitable."
"You can never think security doesn't matter, even if financial details are not on the app," he added. "There is the idea of reputational harm if personal details were leaked and captured. The consumer blames the company when malicious actors are seeking financial or personal details or something like loyalty points."
An "all-too-common scenario" unfolds when a retailer makes the time to market the top priority for a mobile app, and the second priority becomes "whatever is broken," said David Mattei, senior analyst with Aite Group. "That [broken part] usually is no fraud controls."
Before joining Aite Group, Mattei said he had a national supermarket chain client that rolled out a mobile app with online ordering capabilities without fraud controls on it.
"But this was their first mobile app and time to market was everything for them," he said. "They came to me rather desperate because fraud rates were so high and executive management was threatening to shut down the app. We were able to help them mitigate the losses, but unfortunately, fraud functionality was an afterthought."
Julie Conroy, research director and fraud expert with Aite Group, has also seen many cases of mobile retail apps gone awry because of security weaknesses. "A large quick-service retailer was doing OK" with its mobile app "until they launched a reloadable gift card capability into their mobile app," Conroy said. "Overnight, they saw their fraud rate skyrocket as the organized crime rings targeted one of their favorite vulnerability points — gift cards."
It all comes back to the safety net that security providers have preached for the better part of a decade when it comes to payments security: The mobile apps require a layered approach to safety.
Those layers include code hardening to protect code at rest, runtime application self-protection to protect apps in use, and real-time mobile threat intelligence.
"It is the responsibility of the retailer to understand and be aware of this and ask the right questions," Guardsquare's Goodes said. "They have to define this as a mandatory requirement.
"What we are trying to accomplish here is to raise the awareness of the need for security as the top priority. If it isn't, you are just being naive."





