The most sophisticated cyberattacks can begin with something as simple as a text message.
It's more common in retail than in other industries for the attacker to use text messaging to trick a retail employee into initiating a money transfer, according to the 2021 Verizon Data Breach Investigations Report.
"Don't get us wrong, the phishing lure is still effective here," researchers wrote. "It is difficult to determine if the targeting of employees via pre-texting is a sign that criminals are having to work harder for the money, or if it is just simpler for the attackers to dupe employees into committing fraud on their behalf."
The retail industry endured 725 security incidents in 2020, with 165 of them resulting in a confirmed data disclosure,
With criminals motivated to seek retail targets as a way to cash in on exposed payment card data and personal information, Verizon cited system intrusion, social engineering and basic web application attacks as being the most common in 77% of the retail breaches.
Through the work of 83 contributing organizations, the Verizon investigators analyzed 79,635 security incidents across various industries, of which 29,207 met standards for further research — with 5,258 being confirmed breaches highlighted for data in this year's report.
The threats came from external sources in 84% of breaches, while 17% were internal, 2% were noted as having multiple breaches, and 1% utilized partners in the crimes. Nearly all of the retail breaches were financially motivated, with only 1% cited for different motives.
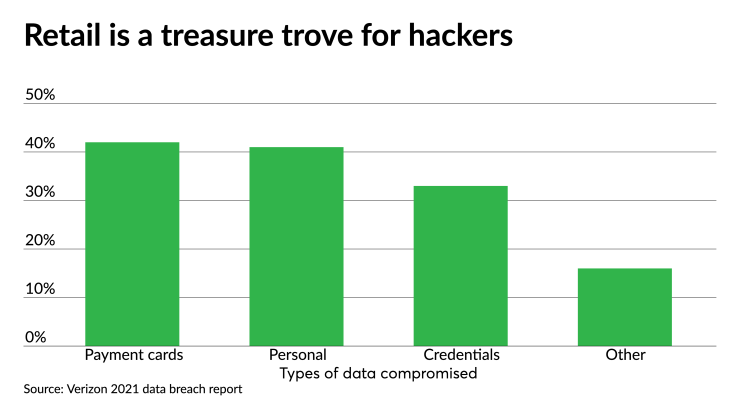
Pursuit of payment card data and other personal information or credentials remained a high priority for hackers.
Payment data was compromised in 42% of retail breaches, while personal information was obtained in 41% and access credentials in 33%.
"We've said it before and we'll say it again — everyone loves credentials," investigators said. "Credentials are the glazed doughnut of data types."
The top protective controls in the retail sector were security awareness and skills training for employees, the report noted. Others were secure configuration of enterprise assets and software, as well as access control management.
Verizon also studied cases in food services, arts and entertainment, education, financial and insurance, healthcare, information services, manufacturing, mining, public administration and professional, scientific or technical services.
Overall, 85% of breaches involved a human element, the research found, with phishing present in 36% of breaches, up from 25% the previous year. Business e-mail compromises were the second most common form of social engineering — fueling an increase of 15 times as many misrepresentation attacks.
The main attack vector was assaults against web applications, cited in more than 80% of breaches.
Human errors leading to breaches decreased percentage-wise to 17% from 22% the year before, but increased in volume from 883 to 905 breaches.
In noting "some things never change," Verizon researchers said they found 61% of breaches involved credential data, meaning passwords were easy to penetrate.
That said, 14% of simulated breaches had no impact. "But don't count on that for your organization's security plan," the report said. "The median for incidents with an impact was $21,659, with 95% of incidents falling between $826 and $653,587."
In reviewing the past year, researchers noted the continued cyber espionage targeting cloud environments by the Chinese menuPass threat actor and others, including an assessment of more than 200 cyber operations by the GRU (Russian military intelligence).
The report cited the
“This report continues to provide eye-opening details of the perilous world organizations must operate in and it appears to be getting worse," Tom Garrubba, chief information security officer of third-party risk assessor Shared Assessments, said in a media statement. "As we all see a flood of breaches soaking various industries, organizations need to realize the importance of preparation and practice against such cyber threats."
Every attempt has to be made by businesses and their security vendors to ensure "a cyber A-game” and review the efficacy of critical cyber processes such as access assignments, monitoring, and log reviews constantly to identify vulnerabilities, Garrubba added.
As it does most years, the Verizon report stirs reaction in the security community through sheer numbers.
“There were 3.3 billion malicious login attempts," Baber Amin, chief operating officer of security firm Veridium, said in a media statement.
"Think about that," Amin added. "World population is 7.6 billion and 61% of breaches involved credential data. This is why we and other experts urge organizations to use passwordless authentication."
Hackers cannot "attack, steal, reuse, share, write down or divulge, something they don’t have," Amin noted. "No password means no phishing, no credential stuffing, and no human error from forgotten passwords, shared passwords, reused passwords or weak passwords."
Tighter security and fewer passwords to hack is even more vital, Amin said, because there are more remote workers, more applications in the cloud and more business logic available via APIs.





