-
Data breaches aren't going away, as Bank of America and Citigroup can attest. A group of institutional, tech and research experts offer 10 steps banks can take now to mitigate the risk.
September 1 -
Visa Inc. has adapted the fraud scoring tool that it uses to vet card-not-present transactions to aid government agencies and private businesses with corporate card accounts.
April 13
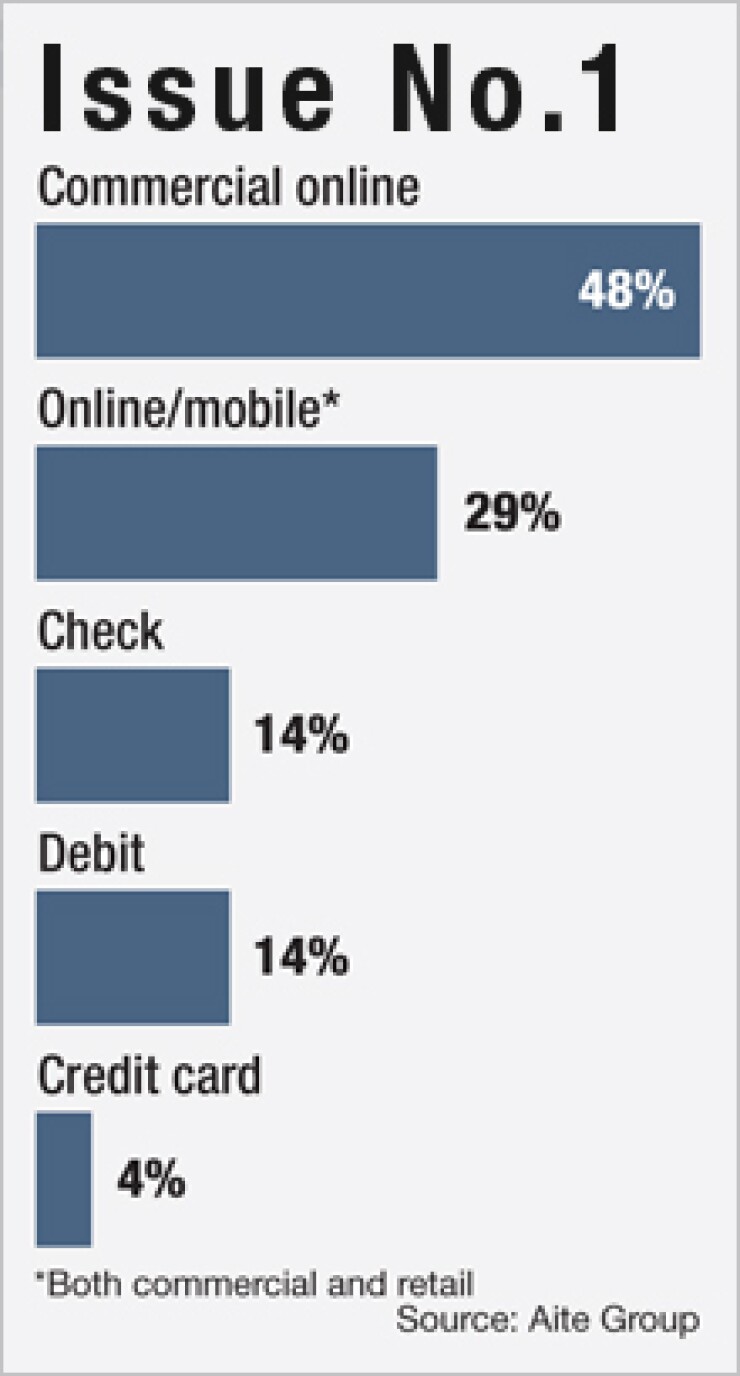
Commercial banks with large corporate clients have no room for error in guarding against the growing number of online attacks specifically targeting them.
Any crack in a bank's security can make it look like it has no security at all if the flaw is found by cyberthieves.
"It is much easier to be a successful bad guy than a successful good guy because a criminal who is successful in one of 100 attempts will make off with a tidy sum," says Julie Conroy McNelley, senior analyst with Aite Group.
"Banks, on the other hand, must seek perfection in their attempts to protect themselves and their customers," McNelley says.
Corporate-account takeovers could result in as much as $210 million in losses this year and could reach $371 million by 2015, according to the first part of a five-part cybercrime report Aite Group is releasing through early 2012.
"The commercial online and mobile channels need the highest priority for fraud protection," McNelley says.
Nearly half of banks surveyed said that protecting online access to corporate accounts is their highest priority.
Fraud at the consumer point of purchase represents "a steadily dripping faucet" by taking a little money all of the time, but commercial-account fraud represents "a big boulder that falls on you" because of the loss of dollars and the domino effect on a bank's tarnished reputation, she says.
A corporate-account takeover often originates when an employee, such as the company controller, logs on to the company's online banking website to transfer funds or confirm deposits after having surfed the Web or opened an email attachment that downloads key-logger malware, McNelley says.
"The criminal will see every keystroke the controller is making on the banking website and will stay there until he is off, and then drain the account," she says.
Hackers could release as many as 25 million new strains of malware by the end of 2011, and the total could grow to 87 million by the end of 2015, the report says.
Though cybercrime is on the rise, so, too, is the number of defenses financial institutions use to fight back, the report notes.
Layered security far more common at banks than it was just five years ago, and many of the leading financial institutions have used that approach for several years, the report says.
Large corporate accounts are not the only targets. The Federal Bureau of Investigation identified 20 incidents between March 2010 and April 2011 in which the online banking credentials of small to midsize businesses were compromised and used to initiate wire transfers to Chinese economic and trade companies, the report says.





