-
Cybercriminals' distributed denial of service exploits are getting more targeted and sophisticated.
April 23 -
Hackers are attacking companies with multiple motives and multiple attack vectors, the widely read annual security report finds. Phishing remains effective and cyber-threat sharing efforts need to speed up.
April 14 -
There's almost no good way of tell a bank customer that her personal data's been stolen. But some banks do a particularly bad job of communicating during a security incident.
October 7
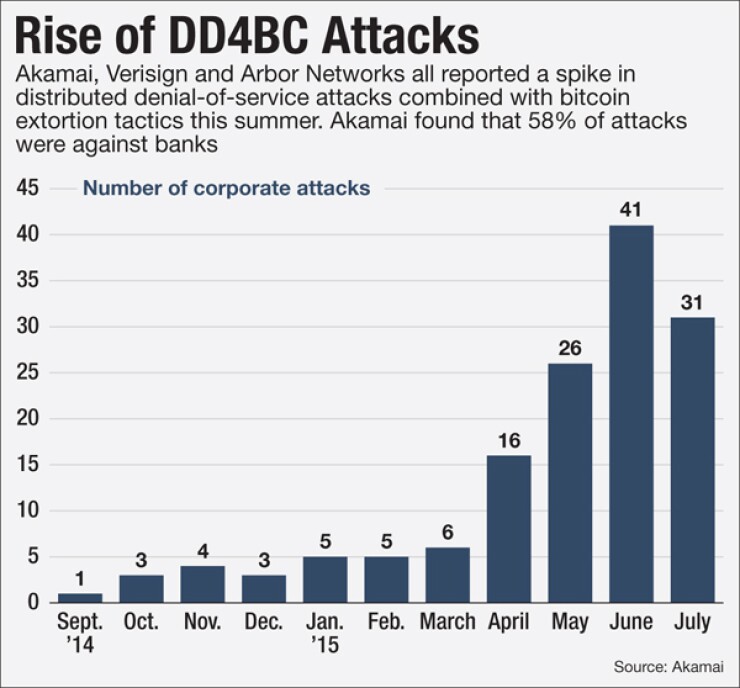
It sounds like a movie plot, but it's all too real: a group with the handle DD4BC tries to hold corporations hostage, threatening distributed denial-of-service attacks unless it is paid a ransom in bitcoins.
Comprehensive data is hard to come by, but security vendor Akamai Technologies reported a spike in such attacks from April through June before they eased a bit in July. Its rivals Arbor Networks and Verisign have detected similar patterns, and the Financial Industry Regulatory Authority recently sent warnings to companies to be on guard.
Casinos and certain other businesses have been dealing with the problem for a decade, but the number of attacks aimed at financial services firms has risen. According to Finra, several financial services and broker-dealer firms were targeted by DD4BC in June alone.
"What is new is their focus on the financial sector and [related entities], including, apparently, government agencies," said Rik Turner, a senior analyst at Ovum. "The other thing is that the volume and frequency of their attacks appear to be on the increase."
For those reasons it is a worthwhile time to examine these attacks, the newest wrinkles in them and tips on prevention, detection and remediation.
How DD4BC Works
A successful DDoS attack renders a website useless by overwhelming it with incoming messages. DD4BC's attacks often begin with an email demanding payment in bitcoins to avoid a disruptive DDoS attack. If that email is ignored, a new email arrives within hours and increases the payment demand, at which time a one- to five-gigabit DDoS attack is launched.
"Think of it as a shot across the bow," said Josh Ray, vice president for Verisign iDefense.
The group might wait another 24 hours for the victim to pay the ransom before launching a larger DDoS attack, anywhere from 10 to 40 gigabits, and sustaining it for about an hour.
There is an increase in unskilled actors using DDoS-for-hire services that are able to conduct larger attacks, Ray said.
"The demand is high for these types of services, and the price is low," he said.
However, it is hard for investigators to identify the source of the attacks. And the fate of the victims has varied.
"There were a couple of companies that reacted too late based on where the email was sent," said Lisa Beegle, security customer success manager at Akamai. In some cases, the note was sent to general mailboxes, so the companies were hit with a DDoS attack before they uncovered the emails.
Some organizations did not even notice when they were attacked; they attributed slow website-response times to network degradation. Many of Akamai's customers moved their web traffic to its network for protection as soon as they received the notifications.
Currency Complication
In an extortion note Akamai shared in its report, the DD4BC group asks its target for 24 bitcoins, which equaled $5,548 in late September.
The demands for bitcoin could be especially troublesome for some bankers.
"If you receive a ransom note stating, 'You have to pay us 40 bitcoin,' you might not even know what bitcoin is," Ray pointed out. "So even the method of making the payment could cause some type of angst."
The amounts sought are small. However, "it's not necessarily about the money itself -- it's about following through with the actual attack and target," Beegle noted.
What is the attackers' principal motive? According to Beegle, the overall goal is to harm the targets. Getting the money is an added win.
Latest Twist
The new wrinkle in DDoS attacks is the rise of DD4BC, a named group that has to be taken seriously. "There is true credibility in that the organizations that were targeted were attacked," Beegle said.
The frequency and volume of DD4BC attacks have multiplied.
Verisign saw 34% more attacks against its customer base in the first half of 2015, and attack sizes grew by about 52% from the first to the second quarter.
Banks were high on the list of targets, according to the experts. Akamai has found that 58% of attacks are directed at financial services companies. Verisign saw a smaller but still significant percentage of incidents targeted at banks, as attackers shifted their attention from previous marks like cryptocurrency exchanges and gaming entities.
"For the third quarter in a row, in the second quarter of this year we saw DDoS attacks focused on [information technology] services, cloud and [software-as-a-service] companies, and that represented a third of all the mitigation activity we handle," Verisign's Ray said. "Closely behind that was the financial and payment sector, which accounted for 22-23% of attacks that were mitigated by Verisign." That latter figure was up 18% from the first quarter.
Most of the DDoS attacks came from the DD4BC group, Ray said.
What to Do About It
Companies need to decide ahead of time what they would do if they were to receive a ransom note. Experts advise against paying ransoms. Some organizations that have paid the bitcoins have been attacked anyway, and some have been retargeted.
"Basically all [banks] can do is strengthen their DDoS-mitigation capabilities to the point where it becomes economically unviable to attack them, leading potential attackers to target others instead because they're easier," Turner said.
He invoked the popular analogy involving two campers attacked by a bear, in which one of the campers realizes all he has to do to survive is outrun the other guy.
"That's the horrible reality of DDoS protection, unfortunately," he said.





